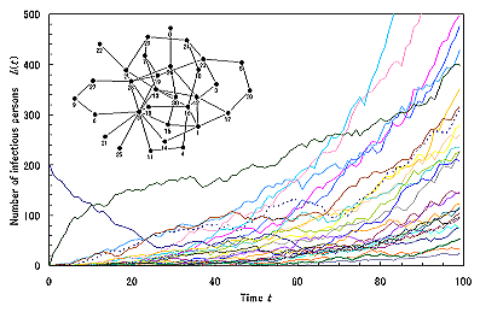
Typical public health surveillance records include a multi-dimensional time series of the cumulative number of newly diagnosed cases of diseases. The diseases range from common cold, seasonal flu and measles, to rare but deadly infectious diseases. The total number of cases which are reported from hospitals in a geographic region indicates the activity level of the disease in that geographic region. World Health Organization updates and publishes such a dataset frequently.
The dataset can be analyzed most suitably by a combination of a meta-population network model and an epidemiological compartment model. The model formulates the spatial movement of hosts (as well as pathogens) and the temporal changes in infection and recovery. This is a class of so-called reaction-diffusion processes which describes the reaction and diffusion of information or substance over a network. The model is mathematically a system of stochastic differential equations.
By solving the equations analytically and numerically, we can determine epidemic parameters and a transmission topology, discover unknown critical spreaders, detect a change point in the transmission trend, and identify the origin of the transmission. Mathematically most of these tasks are categorized in a class of inverse problems. Analysis of newly emerging infectious diseases like SARS in 2003 and a swine flu in 2009 is of particular interest in the point of view of improving a public health intervention program. The solution can also be applied to the study of a bio-terrorism, computer viruses, the diffusion of rumors, or the spread of propaganda.
2. Systems Economics
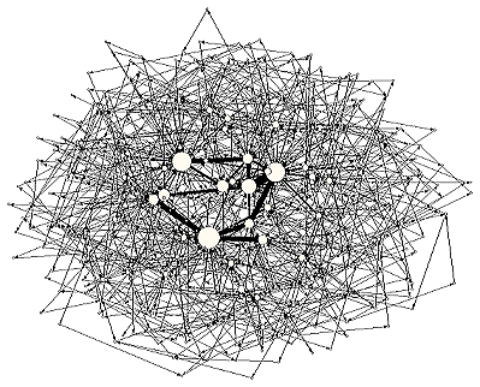
The European sovereign debt crisis has impaired many European banks. European Banking Authority made a warning announcement that European banks are short of equity capital summing up to EUR 114.7 billion, and presented a recapitalization plan in December 2011. The financial distress on some European banks may transmit to banks across country borders, and causes a knock-on default of banks and financial institutions worldwide. Indeed, many globally operating financial institutions ended in bankruptcy in the financial crisis which ensued from the collapse of the subprime mortgage market in 2007.
Since then, supervisors and other relevant authorities have directed a great effort at comprehending the risk which is hidden behind globally interlinked financial institutions and at finding the solution to contain the catastrophic worldwide transmission of distress. The investment porfolio of@banks and financial institutions and the structure of the bank credit network govern the response of the entire financial system to the transmitting distress ensueing from sudden fluctuations in a market. For these purposes, a computer simulation model is developed to analyze the risk of insolvency of banks and defaults in a knock-on default. With the computer simulation model, we can manage investment portfolio of , analyze the transmission of financial distress, and contain the contagion of a worldwide financial system.
3. Reflective Communication Analysis
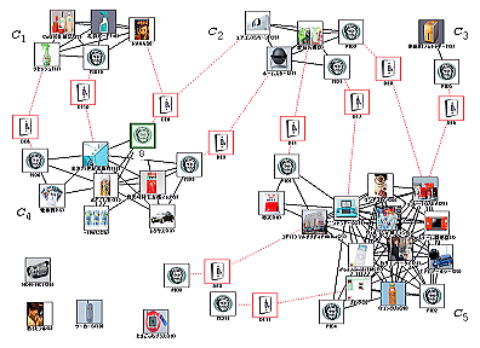
Every person has unique preferences that form the basis of the person's decision-making and consequent behaviors. However, when requested to describe the details of a preference that results in a behavior of particular interest to others, the person often fails to verbally explain. The person is not aware of all aspects of the preference. By understanding such unconscious influences, the person's private and social lifestyles can be re-designed. If they know the consumers' unconscious preferences, vendors can turn to new concepts, unfamiliar products, and emerging services to reach the consumers.
Reflection in cognitive science and computer-mediated communication are theoretical guides to approach unconscious preferences. The abilities to recognize and understand oneself, discover something unexpected, and create something new are founded on constructive perception. Constructive perception is the ability to perceive the visual characteristics of elements, the relationships between the elements, and the empty relevant space between the elements in diagrams, sketches, or drawings. Visualization and verbalization play important roles in becoming aware of a person's present perception, and in changing it. Perception is a process used to interpret sensory signals from the outside.
We can prompt consumers to become aware of his or her unconscious preferences on products and services, and convey them to designers of products and services in the form of verbal explanation.
4. Social Network Analysis
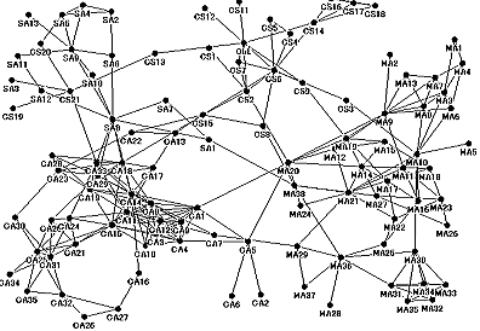
Globally networked clandestine organizations such as terrorists, criminals, or drug smugglers are great threat to the civilized societies. Terrorism attacks cause great economic, social and environmental damage. Governments make great efforts in the active non-routine responses to the attacks as well as the damage recovery management. The short-term target of the responses is the arrest of the perpetrators.
The long-term target of the responses is identifying and dismantling the clandestine organizational foundation which raises, encourages, and helps the perpetrators. The threat will be mitigated and eventually eliminated by discovering covert wire-pullers and critical conspirators of the clandestine organization. The difficulty of such discovery lies in the limited capability of surveillance. Information on the wire-pullers and critical conspirators is hardly obtainable because it is intentionally hidden by the organization.
Let's look at an example in the 9/11 terrorist attack in 2001. Mustafa A. Al-Hisawi was alleged to be a wire-puller who had acted as a financial manager of Al Qaeda. He had attempted to help terrorists enter the United States, and provided the hijackers of the 4 aircrafts with financial support worth more than 300,000 dollars. Furthermore, Osama bin Laden is suspected to be a wire-puller behind Mustafa A. Al-Hisawi and the conspirators behind the hijackers. These persons were not recognized as wire-pullers at the time of the attack. They were the covert nodes to discover from the information on the collaborative activities of the perpetrators and conspirators known at that moment.
We can reveal the communication topology in a terrorist organization and discover unknown influential information spreaders in the organization.
Back to top